Crypto Exchanges Halt ERC20 Token Trading Over Smart Contract Vulnerability
Apr 26, 2018, 4:43PMSeveral major cryptocurrency exchanges temporarily suspended all ERC20-related trading after a smart contract vulnerability was discovered.
Several major cryptocurrency exchanges announced they would temporarily suspend all ERC20-related token trading following the discovery of a security vulnerability named "batchOverflow". The bug could have potentially allowed hackers to withdraw enormous amounts of ERC20 tokens from vulnerable user wallets. After conducting security updates, some exchanges have already resumed ERC20 trading.
The batchOverflow bug was discovered by Blockchain security company PeckShield, which detected two suspicious BEC transactions on April 22, both for excessive amounts of tokens. The bug became a serious issue once the same system vulnerability was exploited to generate over $5 octodecillion (1 followed by 57 zeroes) worth of MESH tokens. An attempt to steal such a ridiculous amount of money may indicate that this was a white hat attack, not intended to work, but rather to alert exchanges to the bug.
Bug Anatomy
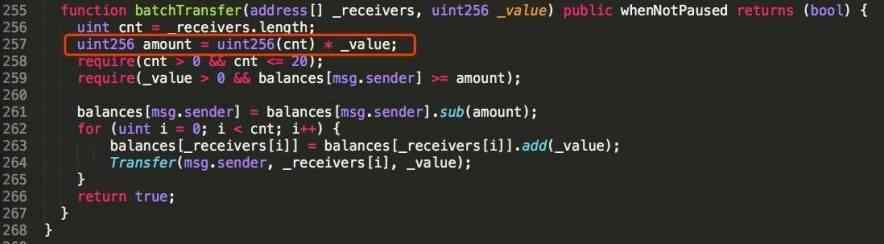
Fig. 1 Vulnerability in the batchTransfer function.
Smart contracts vulnerable to the attack possessed a function called batchTransfer, seen in the image above. The bug exploited the fact that the amount variable (line 257) is calculated as a product of a parameter called cnt and the transaction amount parameter called _value. Since the _value parameter can be any arbitrary 256bit integer (possibly even a ridiculously big number), by entering two _receivers into the batchTransfer function using an enormous transaction _value, the amount variable could be made zero.
Once the amount variable has been zeroed, the hacker could bypass the security checks written in lines 258-259 and, as shown in lines 262-265, both _receivers balances would be added by the ridiculously large _value, without any cost to the attacker.
Further technical details on the issue can be found in a report published by PeckShield.
Ethereum's ERC20 Standard Was Not Vulnerable
According to PeckShield, the smart contract vulnerability was not related to Ethereum's ERC20 standard, but rather, the security company declared that vulnerable contracts possessed a specific "classic integer overflow problem". The ERC20 tokens declared prone to attack were MESH, UGToken, SMT, SMART, MTC, FirstCoin, GG Token, CNY Token, and CNYTokenPLus.
The real danger here is hypothetical. The fact that such smart-contract-related vulnerabilities exist opens up the possibility that attackers could create stores of the vulnerable tokens out of thin air, and exchange them for BTC, ETH, or other cryptocurrencies, possibly even affecting digital asset prices and undermining people's confidence in the Ethereum ecosystem.
Crypto Exchanges Respond to the Attack
Several major cryptocurrency exchanges responded to the batchOverflow news by temporarily suspending all ERC-20-mediated transactions. However, at the time of this writing, Poloniex, Changelly, as well as most other exchanges, have already resumed operations after conducting the pertinent security checks.
Disclaimer: information contained herein is provided without considering your personal circumstances, therefore should not be construed as financial advice, investment recommendation or an offer of, or solicitation for, any transactions in cryptocurrencies.